Instalar servidor DNS
Introducción
Para la instalación del servidor DNS Bind9 se han seguido los pasos indicados en el siguiente vídeo:
Para la instalación del servidor DNS Bind9 se han seguido los pasos indicados en el siguiente vídeo:
Instalación y configuración del servidor DNS Bind9
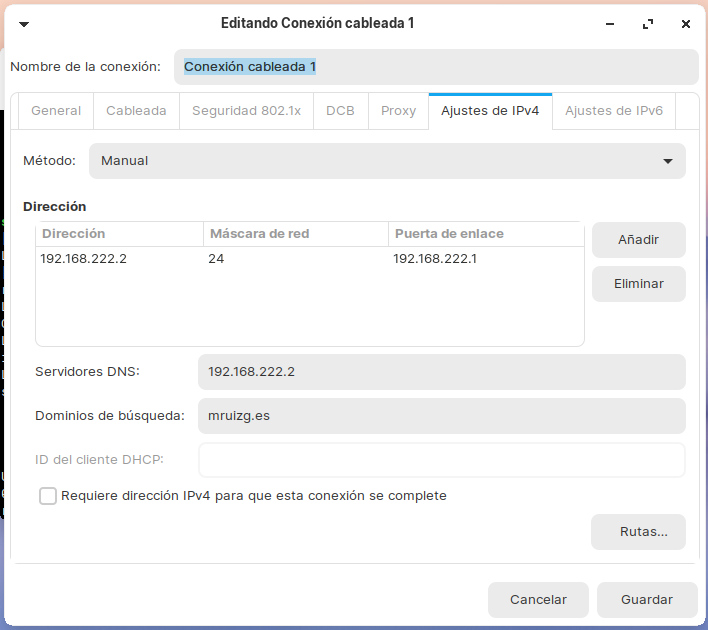 Configuración de red servidor DNS
Configuración de red servidor DNS
Instalar programas necesarios:
1
2
3
4
5
$ sudo -i
# apt update
# apt install bind9
# apt install resolvconf
# resolvconf -u
Ejecutamos la siguiente instrucción para tener permisos de administrador.
1
2
3
4
5
# service network-manager restart
# ifconfig
# ping google.es
# ifconfig
# service bind9 status
Comprobamos que el fichero resolv.conf está bien, sino reiniciamos la máquina:
1
2
3
4
5
6
7
8
# Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8)
# DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN
# 127.0.0.53 is the systemd-resolved stub resolver.
# run "systemd-resolve --status" to see details about the actual nameservers.
nameserver 192.168.222.2
nameserver 127.0.0.53
search mruizg.es
Si aún así no se actualiza, modificamos el fichero head añadiendo el nameserver:
1
2
3
4
5
6
# Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8)
# DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN
# 127.0.0.53 is the systemd-resolved stub resolver.
# run "systemd-resolve --status" to see details about the actual nameservers.
nameserver 192.168.222.2
Modificamos esta línea del fichero nsswitch.conf:
1
hosts: files mdns4_minimal [NOTFOUND=return] dns
Por esta:
1
hosts: dns files mdns4_minimal [NOTFOUND=return]
En named.conf.local añadimos lo siguiente:
1
2
3
4
5
6
7
8
9
10
// zona directa para el dominio mruizg.es
zone "mruizg.es" {
type master;
file "/etc/bind/db.mruizg.es";
};
// zona inversa para la red 192.168.222.0
zone "222.168.192.in-addr.arpa" {
type master;
file "/etc/bind/db.222.168.192";
};
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
;
; BIND data file for mruizg.es zone
;
$TTL 604800
@ IN SOA servidor.mruizg.es. root.mruizg.es. (
2 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
;
IN NS servidor.mruizg.es.
servidor IN A 192.168.222.2
cliente1 IN A 192.168.222.51
router IN A 192.168.222.1
cliente2.mruizg.es. IN A 192.168.222.52
server IN CNAME servidor
correo IN A 192.168.222.2
mruizg.es. IN MX 10 correo
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
;
; BIND data file for mruizg.es zone
;
$TTL 604800
@ IN SOA servidor.mruizg.es. root.mruizg.es. (
2 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
;
IN NS servidor.mruizg.es.
2 IN PTR servidor.mruizg.es.
51 IN PTR cliente1.mruizg.es.
1 IN PTR router.mruizg.es.
52 IN PTR cliente2.mruizg.es.
2 IN PTR correo.mruizg.es.
Comprobamos la sintaxis con los siguientes comandos:
1
2
3
4
5
# named-checkconf /etc/bind/named.conf.local
# named-checkzone mruiz.es /etc/bind/db.mruizg.es
# named-checkzone 222.168.192.in-addr.arpa /etc/bind/db.222.168.192
# service bind9 restart
# service bind9 status
Comprobamos que funciona:
1
2
3
4
# nslookup servidor
# nslookup server
# nslookup 192.168.222.2
# nslookup correo.mruizg.es
Creamos los usuarios mruizgCompras y mruizVentas con la interfaz de usuario:
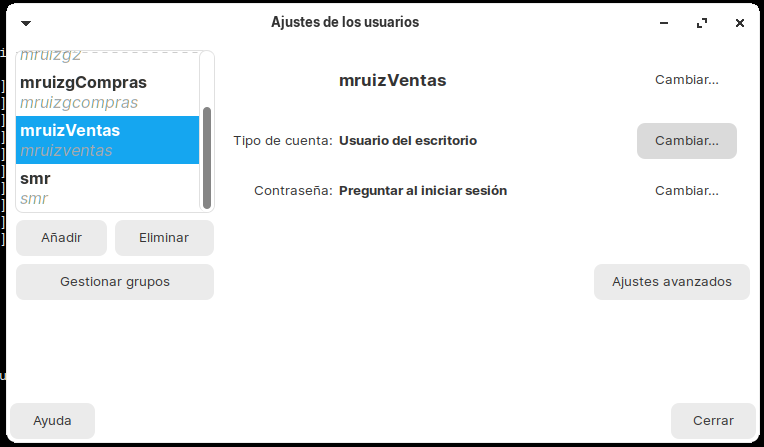 Usuarios mruizgCompras y mruizgVentas
Usuarios mruizgCompras y mruizgVentas
Instalación y configuración del servidor de email Postfix
1
# apt install postfix
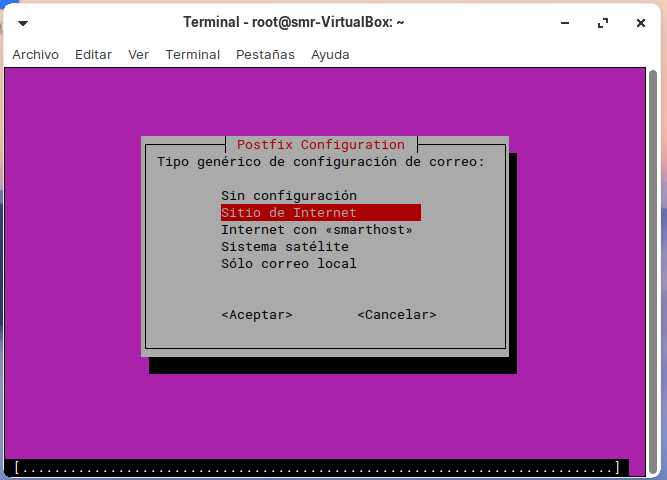 Instalación de Postfix: Postfix Configuration (Parte 1)
Instalación de Postfix: Postfix Configuration (Parte 1)
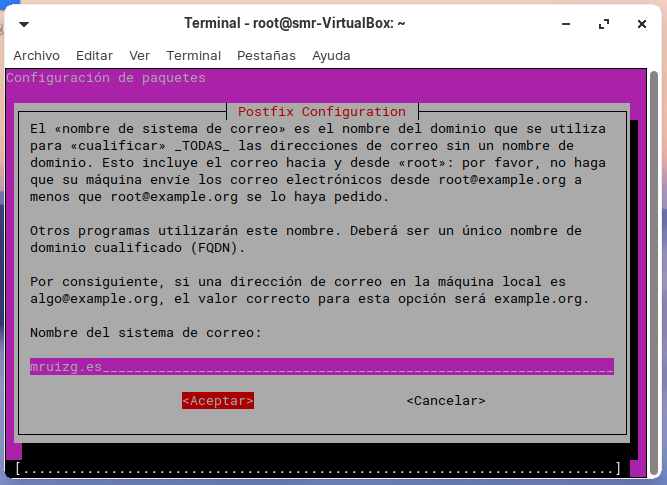 Instalación de Postfix: Postfix Configuration (Parte 2)
Instalación de Postfix: Postfix Configuration (Parte 2)
Comprobamos la versión
1
2
# postconf mail_version
mail_version = 3.3.0
Comprobamos que el servicio está escuchando por el puerto 25:
1
2
3
4
5
6
7
8
9
10
11
12
13
# netstat -lnpt
Conexiones activas de Internet (solo servidores)
Proto Recib Enviad Dirección local Dirección remota Estado PID/Program name
tcp 0 0 192.168.222.2:53 0.0.0.0:* ESCUCHAR 3103/named
tcp 0 0 127.0.0.1:53 0.0.0.0:* ESCUCHAR 3103/named
tcp 0 0 127.0.0.53:53 0.0.0.0:* ESCUCHAR 536/systemd-resolve
tcp 0 0 127.0.0.1:631 0.0.0.0:* ESCUCHAR 562/cupsd
tcp 0 0 0.0.0.0:25 0.0.0.0:* ESCUCHAR 4957/master
tcp 0 0 127.0.0.1:953 0.0.0.0:* ESCUCHAR 3103/named
tcp6 0 0 :::53 :::* ESCUCHAR 3103/named
tcp6 0 0 ::1:631 :::* ESCUCHAR 562/cupsd
tcp6 0 0 :::25 :::* ESCUCHAR 4957/master
tcp6 0 0 ::1:953 :::* ESCUCHAR 3103/named
Comprobamos si el cortafuegos nos está bloqueando el puerto 25 (de entrada) desde una máquina cliente:
1
2
$ nc -zv 192.168.222.2 25
Connection to 192.168.222.2 25 port [tcp/smtp] succeeded!
Comprobamos si el cortafuegos nos está bloqueando el puerto 25 (de salida) desde el servidor:
1
2
3
4
5
# telnet gmail-smtp-in.l.google.com 25
Trying 173.194.76.26...
Connected to gmail-smtp-in.l.google.com.
Escape character is '^]'.
220 mx.google.com ESMTP c8si11219209wri.907 - gsmtp
Escribimos quit para salir.
Comprobamos la carpeta donde se encuentran todos los ficheros de configuración. El fichero que nos interesa es el main.cf:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# ls -l /etc/postfix
total 128
-rw-r--r-- 1 root root 60 feb 13 20:49 dynamicmaps.cf
drwxr-xr-x 2 root root 4096 ago 12 2021 dynamicmaps.cf.d
-rw-r--r-- 1 root root 1503 feb 13 20:49 main.cf
-rw-r--r-- 1 root root 27125 feb 13 20:49 main.cf.proto
-rw-r--r-- 1 root root 4480 ago 12 2021 makedefs.out
-rw-r--r-- 1 root root 6143 feb 13 20:49 master.cf
-rw-r--r-- 1 root root 6143 feb 13 20:49 master.cf.proto
-rw-r--r-- 1 root root 10170 ago 12 2021 postfix-files
drwxr-xr-x 2 root root 4096 ago 12 2021 postfix-files.d
-rwxr-xr-x 1 root root 10123 ago 12 2021 postfix-script
-rwxr-xr-x 1 root root 29522 ago 12 2021 post-install
drwxr-xr-x 2 root root 4096 ago 12 2021 sasl
Hacemos una copia de seguridad del archivo main.cf:
1
cp /etc/postfix/main.cf /etc/postfix/main.cf.original
El archivo original es el siguiente:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
# Debian specific: Specifying a file name will cause the first
# line of that file to be used as the name. The Debian default
# is /etc/mailname.
#myorigin = /etc/mailname
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
readme_directory = no
# See http://www.postfix.org/COMPATIBILITY_README.html -- default to 2 on
# fresh installs.
compatibility_level = 2
# TLS parameters
smtpd_tls_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
smtpd_tls_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
smtpd_use_tls=yes
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
# See /usr/share/doc/postfix/TLS_README.gz in the postfix-doc package for
# information on enabling SSL in the smtp client.
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
myhostname = smr-VirtualBox.mruizg.es
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = $myhostname, mruizg.es, smr-VirtualBox, localhost.localdomain, localhost
Modificamos el fichero main.cf y lo dejamos de la siguiente manera:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
# Debian specific: Specifying a file name will cause the first
# line of that file to be used as the name. The Debian default
# is /etc/mailname.
#myorigin = /etc/mailname
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
biff = no
# appending .domain is the MUA's job.
append_dot_mydomain = no
# Uncomment the next line to generate "delayed mail" warnings
#delay_warning_time = 4h
readme_directory = no
# See http://www.postfix.org/COMPATIBILITY_README.html -- default to 2 on
# fresh installs.
compatibility_level = 2
# TLS parameters
smtpd_tls_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
smtpd_tls_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
smtpd_use_tls=yes
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
# See /usr/share/doc/postfix/TLS_README.gz in the postfix-doc package for
# information on enabling SSL in the smtp client.
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
myhostname = correo.mruizg.es
alias_maps = hash:/etc/aliases
alias_database = hash:/etc/aliases
myorigin = /etc/mailname
mydestination = $myhostname, mruizg.es, localhost.localdomain, localhost
# Añadido por mruizg
mynetworks = 192.168.222.0/24 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
inet_interfaces = all
Comprobamos el fichero mailname contiene el nombre de dominio que tenemos:
1
mruizg.es
Actualizamos el servicio:
1
2
# service postfix reload
# service postfix status
Comprobamos la configuración activa de Postfix:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
# postconf -n
alias_database = hash:/etc/aliases
alias_maps = hash:/etc/aliases
append_dot_mydomain = no
biff = no
compatibility_level = 2
inet_interfaces = all
mydestination = $myhostname, mruizg.es, localhost.localdomain, localhost
myhostname = correo.mruizg.es
mynetworks = 192.168.222.0/24 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
myorigin = /etc/mailname
readme_directory = no
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
smtpd_banner = $myhostname ESMTP $mail_name (Ubuntu)
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
smtpd_tls_cert_file = /etc/ssl/certs/ssl-cert-snakeoil.pem
smtpd_tls_key_file = /etc/ssl/private/ssl-cert-snakeoil.key
smtpd_tls_session_cache_database = btree:${data_directory}/smtpd_scache
smtpd_use_tls = yes
A partir de este momento ya deberiamos ser capaces de enviar y recibir correos.
Enviar correos desde línea de comandos
1
# echo "correo de prueba de mruizg" | sendmail mruizgCompras@mruizg.es
En otra terminal podemos tener los logs para comprobar que todo va bien:
1
# tail -f /var/log/mail.log
Y comprobamos los logs nuevos:
1
2
3
4
5
Feb 13 21:19:54 smr-VirtualBox postfix/pickup[5981]: 38CAD456B6: uid=0 from=<root>
Feb 13 21:19:54 smr-VirtualBox postfix/cleanup[6083]: 38CAD456B6: message-id=<20220213201954.38CAD456B6@correo.mruizg.es>
Feb 13 21:19:54 smr-VirtualBox postfix/qmgr[5982]: 38CAD456B6: from=<root@mruizg.es>, size=273, nrcpt=1 (queue active)
Feb 13 21:19:54 smr-VirtualBox postfix/local[6085]: 38CAD456B6: to=<mruizgCompras@mruizg.es>, relay=local, delay=0.02, delays=0.01/0/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
Feb 13 21:19:54 smr-VirtualBox postfix/qmgr[5982]: 38CAD456B6: removed
Mailbox
Comprobamos la carpeta de Mailbox:
1
2
# postconf mail_spool_directory
mail_spool_directory = /var/mail
Comprobamos que ha llegado el correo en /var/mail/:
1
2
3
4
5
6
7
8
9
10
11
12
13
# cat /var/mail/mruizgcompras
From root@mruizg.es Sun Feb 13 21:19:54 2022
Return-Path: <root@mruizg.es>
X-Original-To: mruizgCompras@mruizg.es
Delivered-To: mruizgCompras@mruizg.es
Received: by correo.mruizg.es (Postfix, from userid 0)
id 38CAD456B6; Sun, 13 Feb 2022 21:19:54 +0100 (CET)
Message-Id: <20220213201954.38CAD456B6@correo.mruizg.es>
Date: Sun, 13 Feb 2022 21:19:54 +0100 (CET)
From: root <root@mruizg.es>
correo de prueba de mruizg
Enviamos un segundo correo:
1
# echo "correo 2 de prueba de mruizg" | sendmail mruizgCompras@mruizg.es
Comprobamos que se apilan los mensajes:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
# cat /var/mail/mruizgcompras
From root@mruizg.es Sun Feb 13 21:19:54 2022
Return-Path: <root@mruizg.es>
X-Original-To: mruizgCompras@mruizg.es
Delivered-To: mruizgCompras@mruizg.es
Received: by correo.mruizg.es (Postfix, from userid 0)
id 38CAD456B6; Sun, 13 Feb 2022 21:19:54 +0100 (CET)
Message-Id: <20220213201954.38CAD456B6@correo.mruizg.es>
Date: Sun, 13 Feb 2022 21:19:54 +0100 (CET)
From: root <root@mruizg.es>
correo de prueba de mruizg
From root@mruizg.es Sun Feb 13 21:25:02 2022
Return-Path: <root@mruizg.es>
X-Original-To: mruizgCompras@mruizg.es
Delivered-To: mruizgCompras@mruizg.es
Received: by correo.mruizg.es (Postfix, from userid 0)
id AAEE8456B7; Sun, 13 Feb 2022 21:25:02 +0100 (CET)
Message-Id: <20220213202502.AAEE8456B7@correo.mruizg.es>
Date: Sun, 13 Feb 2022 21:25:02 +0100 (CET)
From: root <root@mruizg.es>
correo 2 de prueba de mruizg
Envio un correo de prueba a mi correo externo:
1
2
3
# sendmail mruizg@chabacier.es
Subject: Prueba correo externo mruizg
Correo de prueba.
Pulsamos Ctrl+D para enviar y comprobamos los logs:
1
2
Feb 13 21:28:47 smr-VirtualBox postfix/local[6120]: 34D20456BA: to=<root@mruizg.es>, relay=local, delay=0.01, delays=0.01/0/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
Feb 13 21:28:47 smr-VirtualBox postfix/qmgr[5982]: 34D20456BA: removed
Vamos a nuestra cuenta de correo y comprobamos que se ha enviado bien. En este caso, no se envia bien ya que la IP pública que me ha asignado mi ISP está en la base de datos spamhaus.
1
2
3
4
5
6
7
8
9
10
Feb 13 22:40:17 smr-VirtualBox postfix/pickup[5981]: 24468456B9: uid=0 from=<root>
Feb 13 22:40:17 smr-VirtualBox postfix/cleanup[6331]: 24468456B9: message-id=<20220213214017.24468456B9@correo.mruizg.es>
Feb 13 22:40:17 smr-VirtualBox postfix/qmgr[5982]: 24468456B9: from=<root@mruizg.es>, size=297, nrcpt=1 (queue active)
Feb 13 22:40:18 smr-VirtualBox postfix/smtp[6333]: 24468456B9: to=<profesor.mruizg@gmail.com>, relay=gmail-smtp-in.l.google.com[173.194.76.27]:25, delay=20, delays=19/0/0.74/0.26, dsn=5.7.1, status=bounced (host gmail-smtp-in.l.google.com[173.194.76.27] said: 550-5.7.1 [119.12.233.152] The IP you're using to send mail is not authorized to 550-5.7.1 send email directly to our servers. Please use the SMTP relay at your 550-5.7.1 service provider instead. Learn more at 550 5.7.1 https://support.google.com/mail/?p=NotAuthorizedError u15si10538713wrp.505 - gsmtp (in reply to end of DATA command))
Feb 13 22:40:18 smr-VirtualBox postfix/cleanup[6331]: 288D1456BA: message-id=<20220213214018.288D1456BA@correo.mruizg.es>
Feb 13 22:40:18 smr-VirtualBox postfix/bounce[6334]: 24468456B9: sender non-delivery notification: 288D1456BA
Feb 13 22:40:18 smr-VirtualBox postfix/qmgr[5982]: 288D1456BA: from=<>, size=2900, nrcpt=1 (queue active)
Feb 13 22:40:18 smr-VirtualBox postfix/qmgr[5982]: 24468456B9: removed
Feb 13 22:40:18 smr-VirtualBox postfix/local[6335]: 288D1456BA: to=<root@mruizg.es>, relay=local, delay=0.01, delays=0/0/0/0, dsn=2.0.0, status=sent (delivered to mailbox)
Feb 13 22:40:18 smr-VirtualBox postfix/qmgr[5982]: 288D1456BA: removed
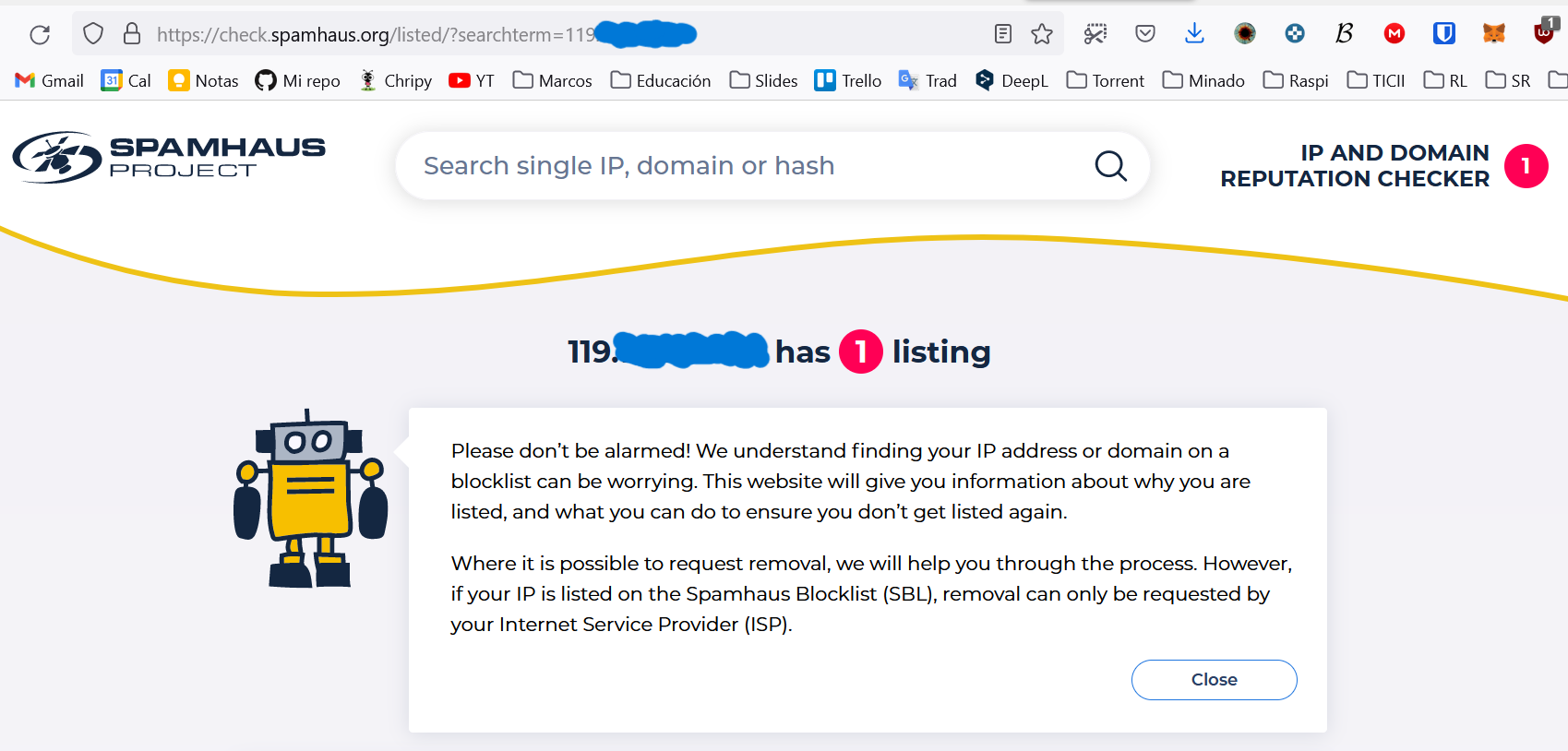 IP bloqueada
IP bloqueada
Intentamos enviar un correo a root@mruizg.es y vemos que no funciona:
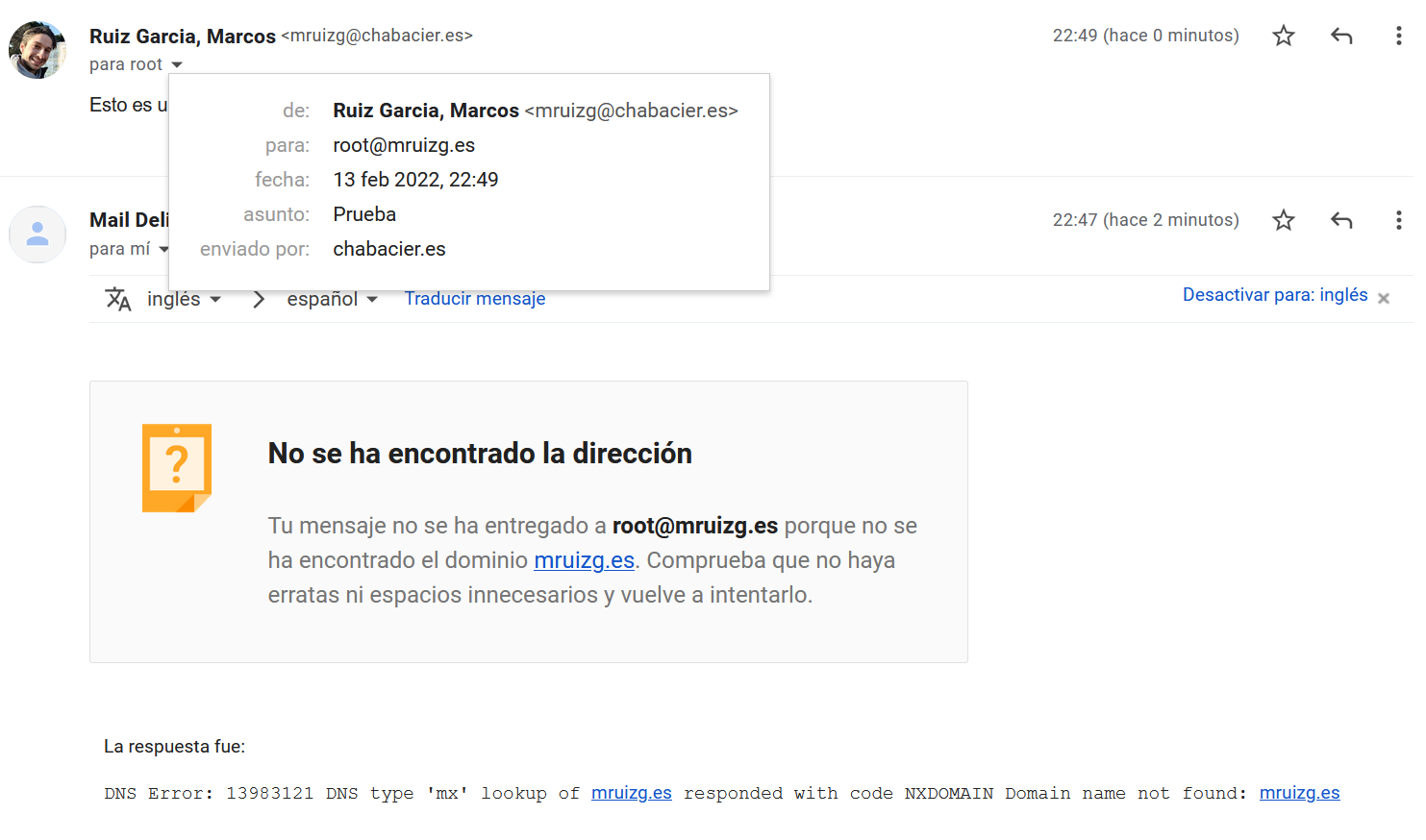 Mensaje de respuesta desde la cuenta del centro: No se ha encontrado la dirección
Mensaje de respuesta desde la cuenta del centro: No se ha encontrado la dirección
Maildir
Añadimos al fichero main.cf la siguiente línea:
1
home_mailbox = Maildir/
Reiniciamos el servicio y comprobamos la configuración:
1
2
3
# service postfix restart
# service postfix status
# postconf -n
Instalamos el mailutils:
1
# apt install mailutils
Enviamos un mensaje:
1
# echo "Subject: correo 3 de prueba de mruizg" | sendmail mruizgCompras@mruizg.es
Y comprobamos en los logs que lo ha guardado en maildir (delivered to maildir):
1
2
3
4
5
Feb 13 22:59:06 smr-VirtualBox postfix/pickup[6598]: 001D6456C0: uid=0 from=<root>
Feb 13 22:59:06 smr-VirtualBox postfix/cleanup[7309]: 001D6456C0: message-id=<20220213215906.001D6456C0@correo.mruizg.es>
Feb 13 22:59:06 smr-VirtualBox postfix/qmgr[6599]: 001D6456C0: from=<root@mruizg.es>, size=282, nrcpt=1 (queue active)
Feb 13 22:59:06 smr-VirtualBox postfix/local[7311]: 001D6456C0: to=<mruizgCompras@mruizg.es>, relay=local, delay=0.02, delays=0.01/0/0/0, dsn=2.0.0, status=sent (delivered to maildir)
Feb 13 22:59:06 smr-VirtualBox postfix/qmgr[6599]: 001D6456C0: removed
Comprobamos que se han creado 3 carpetas en /home/mruizgcompras/Maildir/:
1
2
3
4
5
6
# ls -l /home/mruizgcompras/Maildir/
total 12
drwx------ 2 mruizgcompras mruizgcompras 4096 feb 13 22:59 cur
drwx------ 2 mruizgcompras mruizgcompras 4096 feb 13 22:59 new
drwx------ 2 mruizgcompras mruizgcompras 4096 feb 13 22:59 tmp
Comprobamos que en la carpeta new tenemos un nuevo archivo:
1
2
3
4
root@smr-VirtualBox:~# ls -l /home/mruizgcompras/Maildir/new/
total 4
-rw------- 1 mruizgcompras mruizgcompras 383 feb 13 22:59 1644789546.V801I1a6adfM8376.smr-VirtualBox
Y observamos el correo en sí:
1
2
3
4
5
6
7
8
9
Return-Path: <root@mruizg.es>
X-Original-To: mruizgCompras@mruizg.es
Delivered-To: mruizgCompras@mruizg.es
Received: by correo.mruizg.es (Postfix, from userid 0)
id 001D6456C0; Sun, 13 Feb 2022 22:59:05 +0100 (CET)
Subject: correo 3 de prueba de mruizg
Message-Id: <20220213215906.001D6456C0@correo.mruizg.es>
Date: Sun, 13 Feb 2022 22:59:05 +0100 (CET)
From: root <root@mruizg.es>
Utilizamos el cliente de correo de mailutils:
1
2
3
4
5
6
7
8
9
10
11
12
13
# mail -f /home/mruizgcompras/Maildir/
"/home/mruizgcompras/Maildir/": 1 mensaje 1 nuevo
>N 1 root 10/384 correo 3 de prueba de mruizg
? 1
Return-Path: <root@mruizg.es>
X-Original-To: mruizgCompras@mruizg.es
Delivered-To: mruizgCompras@mruizg.es
Received: by correo.mruizg.es (Postfix, from userid 0)
id 001D6456C0; Sun, 13 Feb 2022 22:59:05 +0100 (CET)
Subject: correo 3 de prueba de mruizg
Message-Id: <20220213215906.001D6456C0@correo.mruizg.es>
Date: Sun, 13 Feb 2022 22:59:05 +0100 (CET)
From: root <root@mruizg.es>
En este momento podemos usar:
qpara quitardpara elminarhpara ver los correos
Enviamos otro correo y comrpobamos que también llega:
1
2
3
4
5
6
7
8
9
10
# echo "Subject: correo 4 de prueba de mruizg" | sendmail mruizgCompras@mruizg.es
# ls -l /home/mruizgcompras/Maildir/new/
total 4
-rw------- 1 mruizgcompras mruizgcompras 383 feb 13 23:07 1644790031.V801I1a6ae2M655146.smr-VirtualBox
# ls -l /home/mruizgcompras/Maildir/cur/
total 4
-rw------- 1 mruizgcompras mruizgcompras 383 feb 13 22:59 1644789546.V801I1a6adfM8376.smr-VirtualBox:2,RS
Instalación y configuración de Dovecot
Instalamos Dovecot y comprobamos su versión:
1
2
# apt install dovecot-core dovecot-imapd
# dovecot --version
Hacemos una copia del archivo principal de configuración:
1
# cp /etc/dovecot/dovecot.conf /etc/dovecot/dovecot.conf.original
El archivo dovecot.conf original es el siguiente:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
## Dovecot configuration file
# If you're in a hurry, see http://wiki2.dovecot.org/QuickConfiguration
# "doveconf -n" command gives a clean output of the changed settings. Use it
# instead of copy&pasting files when posting to the Dovecot mailing list.
# '#' character and everything after it is treated as comments. Extra spaces
# and tabs are ignored. If you want to use either of these explicitly, put the
# value inside quotes, eg.: key = "# char and trailing whitespace "
# Most (but not all) settings can be overridden by different protocols and/or
# source/destination IPs by placing the settings inside sections, for example:
# protocol imap { }, local 127.0.0.1 { }, remote 10.0.0.0/8 { }
# Default values are shown for each setting, it's not required to uncomment
# those. These are exceptions to this though: No sections (e.g. namespace {})
# or plugin settings are added by default, they're listed only as examples.
# Paths are also just examples with the real defaults being based on configure
# options. The paths listed here are for configure --prefix=/usr
# --sysconfdir=/etc --localstatedir=/var
# Enable installed protocols
!include_try /usr/share/dovecot/protocols.d/*.protocol
# A comma separated list of IPs or hosts where to listen in for connections.
# "*" listens in all IPv4 interfaces, "::" listens in all IPv6 interfaces.
# If you want to specify non-default ports or anything more complex,
# edit conf.d/master.conf.
#listen = *, ::
# Base directory where to store runtime data.
#base_dir = /var/run/dovecot/
# Name of this instance. In multi-instance setup doveadm and other commands
# can use -i <instance_name> to select which instance is used (an alternative
# to -c <config_path>). The instance name is also added to Dovecot processes
# in ps output.
#instance_name = dovecot
# Greeting message for clients.
#login_greeting = Dovecot ready.
# Space separated list of trusted network ranges. Connections from these
# IPs are allowed to override their IP addresses and ports (for logging and
# for authentication checks). disable_plaintext_auth is also ignored for
# these networks. Typically you'd specify your IMAP proxy servers here.
#login_trusted_networks =
# Space separated list of login access check sockets (e.g. tcpwrap)
#login_access_sockets =
# With proxy_maybe=yes if proxy destination matches any of these IPs, don't do
# proxying. This isn't necessary normally, but may be useful if the destination
# IP is e.g. a load balancer's IP.
#auth_proxy_self =
# Show more verbose process titles (in ps). Currently shows user name and
# IP address. Useful for seeing who are actually using the IMAP processes
# (eg. shared mailboxes or if same uid is used for multiple accounts).
#verbose_proctitle = no
# Should all processes be killed when Dovecot master process shuts down.
# Setting this to "no" means that Dovecot can be upgraded without
# forcing existing client connections to close (although that could also be
# a problem if the upgrade is e.g. because of a security fix).
#shutdown_clients = yes
# If non-zero, run mail commands via this many connections to doveadm server,
# instead of running them directly in the same process.
#doveadm_worker_count = 0
# UNIX socket or host:port used for connecting to doveadm server
#doveadm_socket_path = doveadm-server
# Space separated list of environment variables that are preserved on Dovecot
# startup and passed down to all of its child processes. You can also give
# key=value pairs to always set specific settings.
#import_environment = TZ
##
## Dictionary server settings
##
# Dictionary can be used to store key=value lists. This is used by several
# plugins. The dictionary can be accessed either directly or though a
# dictionary server. The following dict block maps dictionary names to URIs
# when the server is used. These can then be referenced using URIs in format
# "proxy::<name>".
dict {
#quota = mysql:/etc/dovecot/dovecot-dict-sql.conf.ext
#expire = sqlite:/etc/dovecot/dovecot-dict-sql.conf.ext
}
# Most of the actual configuration gets included below. The filenames are
# first sorted by their ASCII value and parsed in that order. The 00-prefixes
# in filenames are intended to make it easier to understand the ordering.
!include conf.d/*.conf
# A config file can also tried to be included without giving an error if
# it's not found:
!include_try local.conf
La línea 24 con contenido !include_try /usr/share/dovecot/protocols.d/*.protocol nos indica el directorio donde se encuentran los protocolos instalados que están activos. En este caso solo tenemos el protocolo IMAP.
1
2
3
4
# ls -l /usr/share/dovecot/protocols.d/*.protocol
-rw-r--r-- 1 root root 28 feb 13 23:10 /usr/share/dovecot/protocols.d/imapd.protocol
# cat /usr/share/dovecot/protocols.d/imapd.protocol
protocols = $protocols imap
Hacemos una copia de seguridad de los ficheros de configuración 10-ssl.conf, 10-auth.conf y 10-mail.conf:
1
2
3
# cp /etc/dovecot/conf.d/10-ssl.conf /etc/dovecot/conf.d/10-ssl.conf.original
# cp /etc/dovecot/conf.d/10-auth.conf /etc/dovecot/conf.d/10-auth.conf.original
# cp /etc/dovecot/conf.d/10-mail.conf /etc/dovecot/conf.d/10-mail.conf.original
El contenido original del fichero es el siguiente:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
##
## SSL settings
##
# SSL/TLS support: yes, no, required. <doc/wiki/SSL.txt>
ssl = yes
# PEM encoded X.509 SSL/TLS certificate and private key. They're opened before
# dropping root privileges, so keep the key file unreadable by anyone but
# root. Included doc/mkcert.sh can be used to easily generate self-signed
# certificate, just make sure to update the domains in dovecot-openssl.cnf
ssl_cert = </etc/dovecot/private/dovecot.pem
ssl_key = </etc/dovecot/private/dovecot.key
# If key file is password protected, give the password here. Alternatively
# give it when starting dovecot with -p parameter. Since this file is often
# world-readable, you may want to place this setting instead to a different
# root owned 0600 file by using ssl_key_password = <path.
#ssl_key_password =
# PEM encoded trusted certificate authority. Set this only if you intend to use
# ssl_verify_client_cert=yes. The file should contain the CA certificate(s)
# followed by the matching CRL(s). (e.g. ssl_ca = </etc/ssl/certs/ca.pem)
#ssl_ca =
# Require that CRL check succeeds for client certificates.
#ssl_require_crl = yes
# Directory and/or file for trusted SSL CA certificates. These are used only
# when Dovecot needs to act as an SSL client (e.g. imapc backend). The
# directory is usually /etc/ssl/certs in Debian-based systems and the file is
# /etc/pki/tls/cert.pem in RedHat-based systems.
ssl_client_ca_dir = /etc/ssl/certs
#ssl_client_ca_file =
# Request client to send a certificate. If you also want to require it, set
# auth_ssl_require_client_cert=yes in auth section.
#ssl_verify_client_cert = no
# Which field from certificate to use for username. commonName and
# x500UniqueIdentifier are the usual choices. You'll also need to set
# auth_ssl_username_from_cert=yes.
#ssl_cert_username_field = commonName
# DH parameters length to use.
#ssl_dh_parameters_length = 1024
# SSL protocols to use
#ssl_protocols = !SSLv3
# SSL ciphers to use
#ssl_cipher_list = ALL:!LOW:!SSLv2:!EXP:!aNULL
# Prefer the server's order of ciphers over client's.
#ssl_prefer_server_ciphers = no
# SSL crypto device to use, for valid values run "openssl engine"
#ssl_crypto_device =
# SSL extra options. Currently supported options are:
# no_compression - Disable compression.
# no_ticket - Disable SSL session tickets.
#ssl_options =
Ponemos ssl = no y comentemos las siguientes dos líneas como se muestra a continuación:
1
2
# ssl_cert = </etc/dovecot/private/dovecot.pem
# ssl_key = </etc/dovecot/private/dovecot.key
Vamos a /etc/dovecot/conf.d/10-auth.conf y ponemos disable_plaintext_auth = no.
Descomentamos la línea mail_location = maildir:~/Maildir y comentamos # mail_location = mbox:~/mail:INBOX=/var/mail/%u para que Postfix y Dovecot tengan la misma configuración.
Reiniciamos el servicio:
1
2
# service dovecot restart
# service dovecot status
Instalamos Thunderbird si no lo tenemos ya instalado:
1
# apt install thunderbird
Comprobamos que la configuración del cliente es la siguiente:
 Configuración de red del cliente Zorin OS Lite
Configuración de red del cliente Zorin OS Lite
Hacemos un nslookup para comprobar la configuración del cliente:
1
2
3
4
5
6
7
$ nslookup correo.mruizg.es
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
Name: correo.mruizg.es
Address: 192.168.222.2
Thunderbird en el servidor
Añadimos el usuario y la contraseña y la configuración se autodetectará:
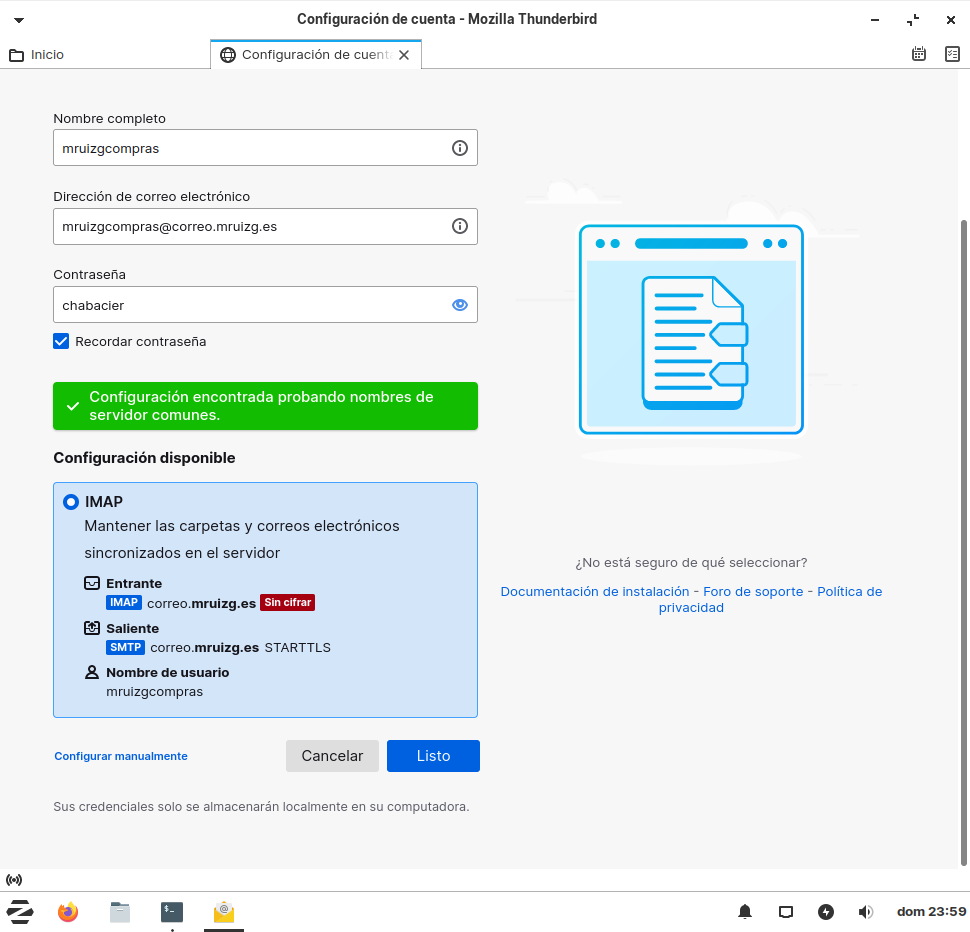 Correo y contraseña en Thunderbird. Configuración autodetectada.
Correo y contraseña en Thunderbird. Configuración autodetectada.
 Inbox de Thunderbird con la cuenta mruizgcompras@mruizg.es
Inbox de Thunderbird con la cuenta mruizgcompras@mruizg.es
Thunderbird en el cliente
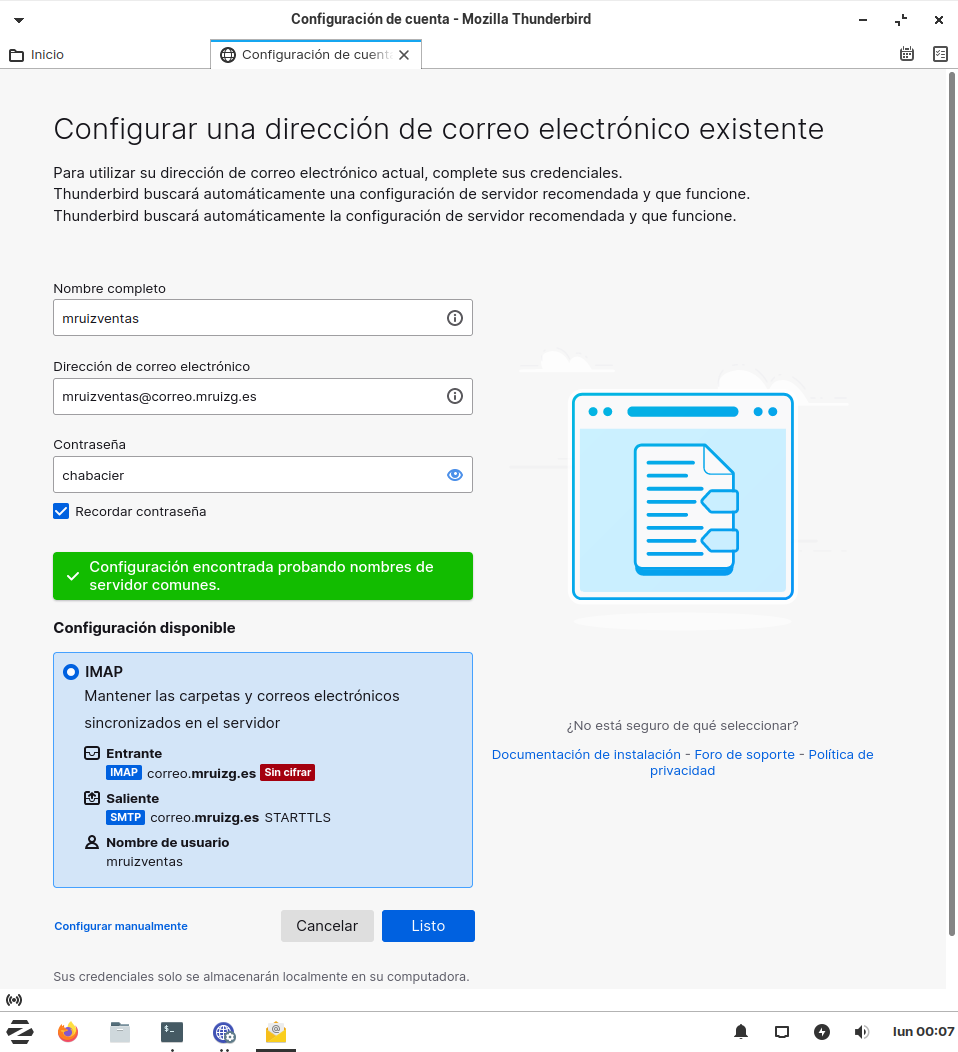 Login en Thunderbird desde cliente con mruizventas@mruizg.es
Login en Thunderbird desde cliente con mruizventas@mruizg.es
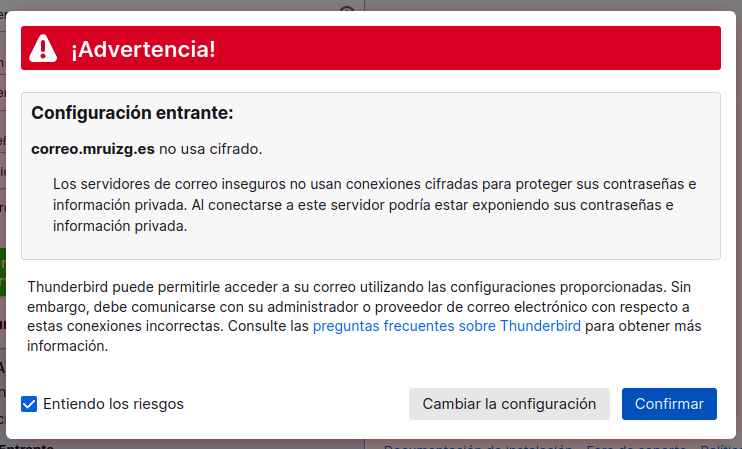 Advertencia de seguridad
Advertencia de seguridad
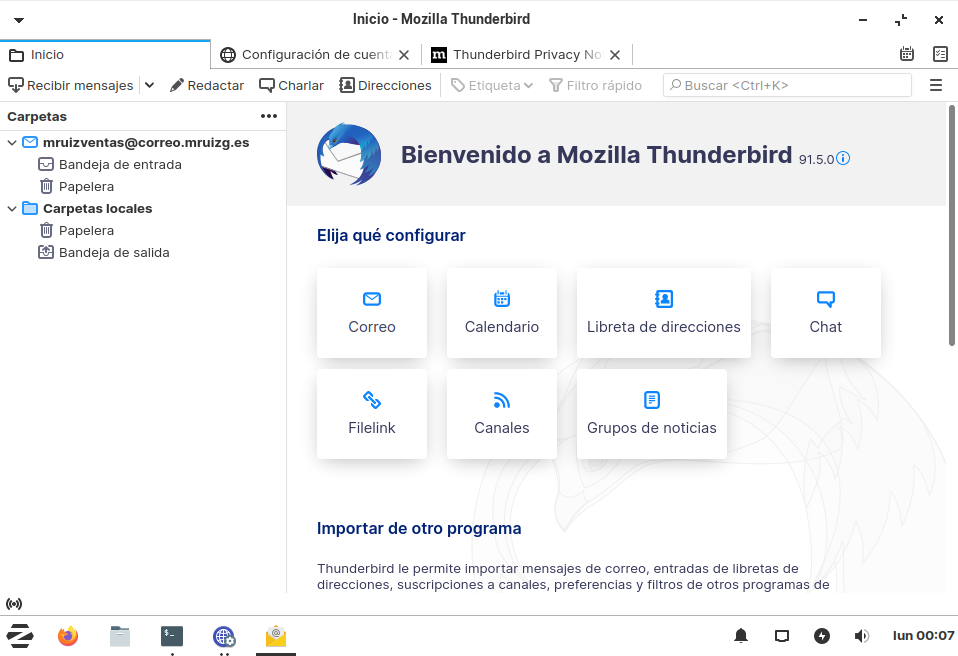 Inbox de Thunderbird con la cuenta mruizventas@mruizg.es
Inbox de Thunderbird con la cuenta mruizventas@mruizg.es
Prueba de funcionamiento
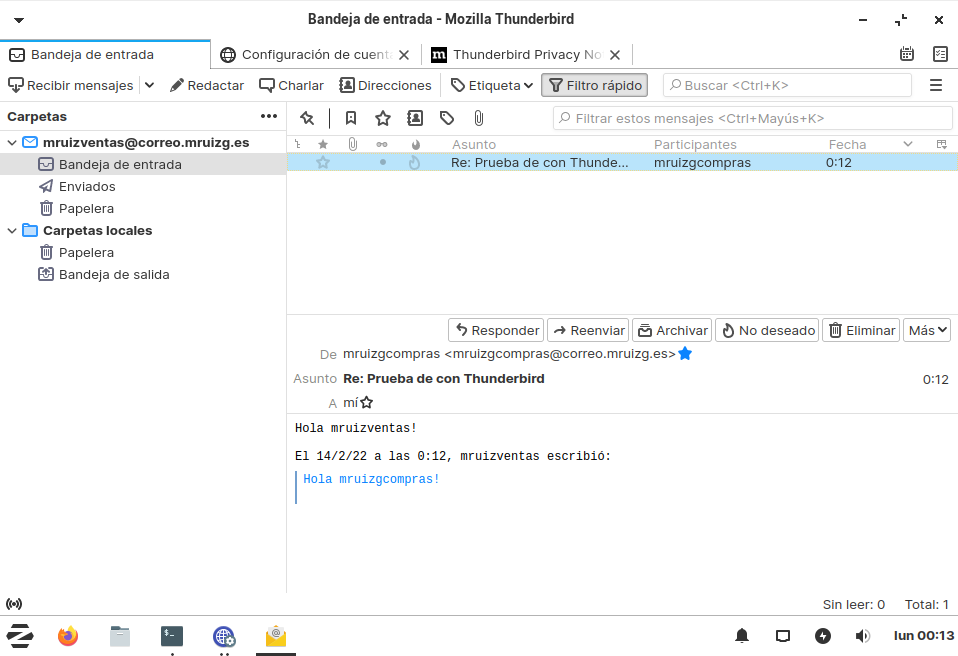 Prueba de funcionamiento con Thunderbird
Prueba de funcionamiento con Thunderbird